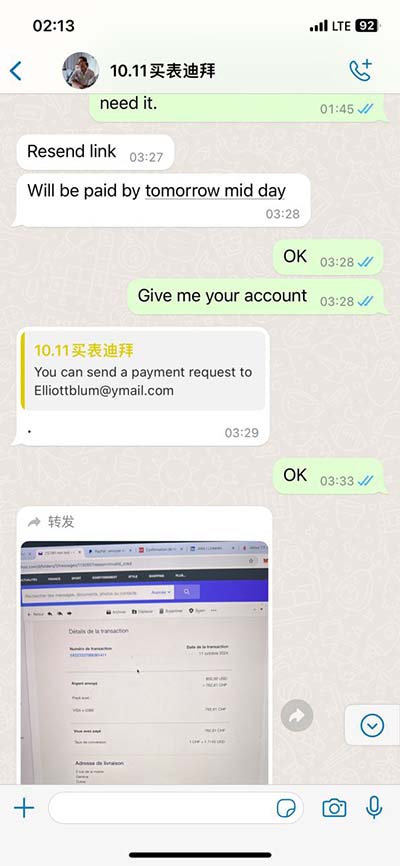
chanel mysql attack | SQL Injection Attack: How It Works, Examples and Prevention chanel mysql attack A database belonging to the famed perfume and fashion brand is believed to have been compromised by a hacker or hackers at some point between August 5 and 6. Data exfiltrated in the attack and later leaked included some customers' names, birth dates, gender, phone numbers, and shopping history. Level 91 spells are available without restriction. Level 92-93 spells are available if you have a language skill of 25 or more. Level 94-95 spells are available if you have a language skill of 50 or more. Rank 2 spells are obtained by turning in "Alaran Cantrip" items to The Sklyg in Beasts' Domain. These Cantrips drop in all Veil of Alaris zones.
0 · SQL Injection Attack: How It Works, Examples and Prevention
1 · SQL INJECTION ATTACKS: A FOCUS ON USER
2 · How to Prevent SQL Injection in MySQL 8: Explained with Examples
3 · Chanel Apologizes for Data Breach
Industriālās elektronikas un elektrotehnikas institūts. Prakse! Pilnveido savas zināšanas praksē studiju laikā. Mūsu studentiem ir iespēja piedalīties procesu izpētē, iegūt teorētiskās un profesionālās zināšanas gan nacionālos gan starptautiskos uzņēmumos, tādos kā AS Augstsprieguma tīkls, Mercedes-Benz Group AG , AS Sadales tīkls, SIA Allatherm un citi.
This article seeks to show how an attacker can leverage the concept of SQL . A database belonging to the famed perfume and fashion brand is believed to . This guide showcases preventative steps and coding practices to avoid SQL injection attacks in MySQL 8, including coding examples from basic to advanced levels, aiming to protect your application against these malicious attempts. This article seeks to show how an attacker can leverage the concept of SQL Injection attacks with a focus on manipulating user-defined functions found in MySQL relational database.
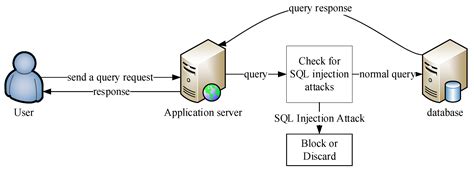
A database belonging to the famed perfume and fashion brand is believed to have been compromised by a hacker or hackers at some point between August 5 and 6. Data exfiltrated in the attack and later leaked included some customers' names, birth dates, gender, phone numbers, and shopping history. SQL Injection attacks (or SQLi) alter SQL queries, injecting malicious code by exploiting application vulnerabilities. Successful SQLi attacks allow attackers to modify database information, access sensitive data, execute admin tasks on .SQL injection (SQLi) is a cyberattack that injects malicious SQL code into an application, allowing the attacker to view or modify a database. According to the Open Application Security Project, injection attacks, which include SQL injections, were the third most serious web application security risk in 2021. Successful SQL injection attacks enable cybercriminals to bypass authentication mechanisms and gain access to sensitive data such as usernames, passwords, credit card details, and more. They can use these details to launch more attacks, such as identity theft, financial fraud, or phishing.
Learn about SQL Injection and explore the types of SQLi. Explore real-life SQL Injection attack examples and find out ways to prevent SQLi.In-band SQL injection is a type of SQL injection where the attacker receives the result as a direct response using the same communication channel. For example, if the attacker performs the attack manually using a web browser, the result of the attack will be displayed in .Out-of-band SQL injection (OOB SQLi) is a type of SQL injection where the attacker does not receive a response from the attacked application on the same communication channel but instead is able to cause the application to send data to a remote endpoint that they control.
Never run the MySQL server as the Unix root user. This is extremely dangerous, because any user with the FILE privilege is able to cause the server to create files as root (for example, ~root/.bashrc). To prevent this, mysqld refuses to run as root unless that is specified explicitly using the --user=root option. This guide showcases preventative steps and coding practices to avoid SQL injection attacks in MySQL 8, including coding examples from basic to advanced levels, aiming to protect your application against these malicious attempts. This article seeks to show how an attacker can leverage the concept of SQL Injection attacks with a focus on manipulating user-defined functions found in MySQL relational database.
A database belonging to the famed perfume and fashion brand is believed to have been compromised by a hacker or hackers at some point between August 5 and 6. Data exfiltrated in the attack and later leaked included some customers' names, birth dates, gender, phone numbers, and shopping history. SQL Injection attacks (or SQLi) alter SQL queries, injecting malicious code by exploiting application vulnerabilities. Successful SQLi attacks allow attackers to modify database information, access sensitive data, execute admin tasks on .SQL injection (SQLi) is a cyberattack that injects malicious SQL code into an application, allowing the attacker to view or modify a database. According to the Open Application Security Project, injection attacks, which include SQL injections, were the third most serious web application security risk in 2021. Successful SQL injection attacks enable cybercriminals to bypass authentication mechanisms and gain access to sensitive data such as usernames, passwords, credit card details, and more. They can use these details to launch more attacks, such as identity theft, financial fraud, or phishing.

SQL Injection Attack: How It Works, Examples and Prevention
Learn about SQL Injection and explore the types of SQLi. Explore real-life SQL Injection attack examples and find out ways to prevent SQLi.In-band SQL injection is a type of SQL injection where the attacker receives the result as a direct response using the same communication channel. For example, if the attacker performs the attack manually using a web browser, the result of the attack will be displayed in .Out-of-band SQL injection (OOB SQLi) is a type of SQL injection where the attacker does not receive a response from the attacked application on the same communication channel but instead is able to cause the application to send data to a remote endpoint that they control.

chanel perfume takashimaya

SQL INJECTION ATTACKS: A FOCUS ON USER
Телефон: 67845007, 27799217: Адрес офиса: Rīga, Kr.Barona iela 120: Подробнее: https://euromobile.lv/kontakti/
chanel mysql attack|SQL Injection Attack: How It Works, Examples and Prevention